Rethinking the Social Construction of Technology through 'Following the Actors': A Reappraisal of Technological Frames
by Christina Prell
University of Sheffield
Sociological Research Online 14(2)4
<http://www.socresonline.org.uk/14/2/4.html>
doi:10.5153/sro.1913
Received: 20 Oct 2008 Accepted: 11 May 2009 Published: 30 May 2009
Abstract
In this paper, I summarize case study research on an information system called Connected Kids. This case study was guided by an approach to technology studies called the 'Social construction of technology' or SCOT Pinch and Bijker (1984). In discussing Connected Kids, I illustrate many of SCOT's main tenents, e.g. the various social interactions that surround and influence technology design. As the paper progresses, however, I focus on one concept in particular, that being SCOT's notion of a 'technological frame,' which is used as a catch-all concept for handling the structural influences in technology design. My discussion and illustration of this concept shows that – whilst technological frames help an analyst understand, in general terms, the role structure(s) play in shaping technology – the 'heterogeneity' of technological frames can cloak the more obvious, and potentially most influential, forces at work in technology design. In the case of Connected kids, the role of resources, and which actors had access to these resources, was critical in pointing Connected Kids down a particular trajectory. Further, this discovery emerged from listening carefully to respondents' comments on the role of resources in their community. These comments, and my own observations on how resource-access propelled certain actors into a leadership position, led to my developing an alternative method for analyzing technological frames. The implications of this analysis are then discussed within the context of SCOT and technology studies more generally.
Keywords: Social Construction of Technology, Technological Frames, Information Technology
Introduction
1.1 Since Pinch and Bijker's (1984) classic paper, "The Social Construction of Facts and Artifacts: or How the Sociology of Science and Technology Might Benefit Each Other," what has come to be known as the Social Construction of Technology (SCOT) has gained a great deal of popularity and positive attention for offering a coherent methodological approach to the study of technology design. Key among the strengths of this approach is SCOT's aim to open up the "black box" of technology, thus revealing the multiple social forces that influence and shape the life-course of a technology. SCOT has also received its share of criticism[1]. Among the criticisms received include the argument that SCOT underplays the importance of structural influences, in particular, the larger structural forces in society such as class, institutions, economic and political systems (Klein and Kleinman, 2002; Russell, 1986; Winner, 1993). Bijker (1995) has responded to these criticisms by developing the concept of a technological frame (TF), a "heterogenous concept" that accounts for material and nonmaterial structures that can influence socio-technical design (Bijker, 1993: 120-121).1.2 In the case study I present here, I demonstrate both the value and shortcomings of the SCOT approach, drawing attention to this issue of structure in relation to technology design. The first half of my paper walks the reader through the development of an IT system through the interpretive lens of SCOT. This IT system is called Connected Kids (located at http://connectedkids.info), and as its website states, Connected Kids is "an online information system" intended for "young people" in upstate New York (accessed May 2009: http://connectedkids.info/AboutCK/index.html). The system was built in collaboration with local government agencies and youth-service organizations, and its planning and development was largely led by members from Rensselaer Polytechnic Institute (RPI) and the University at Albany, SUNY[2]. This paper focuses on the system's early stages of development and those actors involved at that time.
1.3 The second half of my paper re-considers certain structural issues relating to the role of particular actors and the technology's overall development. Here, I look at the role of resource-access and reflect on the suitability of the concept of technological frame for describing, highlighting, and explaining the role of these resources in this project. What emerges from this discussion is less a critique of SCOT's handling of structure, and more a demonstration of an alternative approach to "technological frames" within the context of my own fieldwork observations and interviews. By listening carefully to respondents' comments on the role of resources in their community, and on reflecting on my own observations of how resource-access propelled certain actors into a leadership position, I discuss and show the way in which the "heterogeneity" of technological frames can cloak the more obvious, and potentially more influential, forces at work in technology design.
1.4 Thus, before launching into a description of my case study, I will first offer a summary of SCOT. This description of SCOT's main tenets and concepts will provide a basis upon which to interpret and frame the case that follows. Critical reflection and discussions of this case study and SCOT will happen towards the end.
The Social Construction of Technology (SCOT)
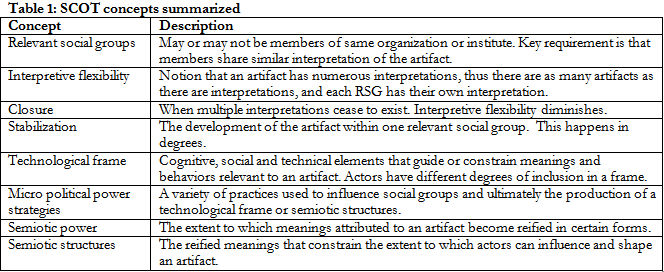
2.1 SCOT is a theory for technological development, and its basic premise states that technologies emerge from social interactions among social groups and actors. SCOT sees no 'right' or 'wrong' technologies, as all technologies have the potential to be shaped differently based on which actors and groups are involved. This flexible quality of technology design, which is the basis of SCOT theory, communicates the message that a technology could have been different, and as such, that technologies in general are pliant creatures, not autonomous ones, and not ones that result from careful, rational planning.2.2 In discussing how technology emerges from these social interactions, the SCOT framework utilises a number of interrelated concepts. These concepts are summarised below, in Table 1.
|
2.3 The first four concepts in Table 1 are considered the first formulation of SCOT as discussed by Pinch and Bijker (1984). The first of these concepts, relevant social groups (RSGs), refers to groups of actors that may or may not belong to the same organisation or institution, but more critically, i.e. "the key requirement," is that all members of this group share the same interpretation of an artifact (Pinch and Bijker, 1984). Actors can be members of different relevant social groups, but each relevant social group has a similar way of perceiving or interpreting a particular artifact. Different social groups have different interpretations of an artifact, and these different interpretations indicate an artifact's interpretive flexibility. Here, the idea is that no one single artifact exists, but rather, there are as many artifacts as there are interpretations, and each relevant social group has their own interpretation.
2.4 Locating relevant social groups involves "two rules: 'roll a snowball' and 'follow the actors'" (Bijker, 1995, pg. 46). Rolling a snowball refers to snowball sampling, a method whereby a researcher starts interviewing selected individuals who are theoretically relevant to a technology, and asks those individuals to nominate others who are also seen as relevant to that technology (Bijker, 1995; MacKenzie and Wajcman, 1999). Through a series of nominations, a researcher follows the actor, and thereby uncovers a larger sample until eventually no new names are mentioned. This dual method for locating relevant social groups may be complemented by a more theoretical one whereby the researcher draws boundaries around social groups and locates social groups through analytical categories developed by the researcher, based on some theoretical justification (Bijker, 1995; Klein and Kleinman, 2002).
2.5 In 'following the actors,' a researcher allows actors to describe their own social group and their perceptions of other social groups. This approach also suggests carefully listening to how actors and groups interpret a technology, and in doing so, one sees how a technology's meaning goes through constant negotiation and renegotiation among the different actors (Martin and Scott, 1992). As interactions among the relevant social groups persist, multiple interpretations of an artifact begin to slowly diminish. This process of diminishing interpretations is referred to as an artifact reaching closure. Closure can be attained through a number of processes: it can occur through groups reaching a consensus of the artifact's meaning[3], it can occur through rhetorical closure, whereby relevant social groups perceive a problem to be solved technically, or closure can be reached through definition of a problem and solution, whereby a technology is positioned and understood to be the solution to a problem (Pinch and Bijker, 1987). Closure occurs when the interpretative flexibility of an artifact diminishes. It occurs between relevant social groups. In addition, closure can take the form of three different configurations, which are the following; 1) no single social group dominates the process, and the groups reach consensus together, 2) one social group dominates the process, asserting its definition of the technology, and 3) two or more groups compete over the meaning of a technology.
2.6 These processes by which closure can take place also contain degrees of stabilization. Stabilization refers to the degree to which an artifact is accepted by an relevant social group; the more homogeneous the meanings attributed to a particular artifact, the higher is the degree of stabilization for a particular artifact within that relevant social group (Bijker, 1993). Thus, stabilization occurs at different points in different relevant social groups, and it is semiotic. An indicator for stabilization is when the names used for an artifact become, over time, more simplified. Degrees of stabilization thus reflects an idea of movement or fluidity, i.e. that an artifact's meaning is acquired via a social process, and it also suggests how these meanings can slowly reach a state of closure. Once closure is reached, an artifact's meaning is rarely re-opened again[4].
2.7 These four concepts provide the basis for SCOT, and they likewise lead an analyst through four stages of the design process. In later texts, Bijker (Bijker and Law, 1992; Bijker, 1993; Bijker, 1995) attempts to expand the SCOT framework to take into consideration issues of power and structure. The remaining four concepts found in Table 1 are those developed by Bijker to address these issues. The first, a technological frame consists of problem solving strategies, values, goals, actors' situations, and tools that guide actors' interactions, thoughts, and behaviors. It includes material, technical, social, and cognitive elements. Everything is included in a technological frame, and yet these elements do not belong to individuals, institutions or systems. Rather then been seeing as characteristics of institutions, individuals or systems, technological frames are seen as located between actors, not in them or above them. At the same time however, technological frames belong to relevant social groups. As actors within a relevant social group interact with one another, they build up a common interpretation of an artifact, and thus likewise build a technological frame. If actors fail to arrive at a similar interpretation, then actors will likewise fail in building a technological frame and establishing a social group. If a technological frame gets built, however, it will then structure the behaviors, thoughts, and interactions among actors in that social group.
2.8 The extent to which a technological frame structures actions depends on the level of inclusion actors have in a particular relevant social group and technological frame. Actors with a high degree of inclusion in a technological frame will interact in terms set by the technological frame while actors with a low inclusion will be less affected by the technological frame. Degrees of inclusion thus imply that actors can be included in more than one frame, just as they can be members of more than one relevant social group.
2.9 Closely related to technological frames is the notion of semiotic power, a process whereby meanings become 'reified in certain forms' through interactions among actors and relevant social groups, and these reified forms act as a semiotic structure that constrains and guide how actors and groups interpret and influence an artifact (Bijker, 1995, p.263). Thus, as a technological frame becomes stronger, it fixes the interpretations of an artifact further, and this fixation of meaning represents both the semiotic structure and the power of this structure. Finally, Bijker sees technological frames and semiotic structures being built through social interaction and micro political power strategies, i.e. a variety of practices used by actors to influence social groups and thus build frames and structures. A common micro political strategy discussed in the SCOT literature is that of enrolment, whereby an actor draws in other actors and/or groups to support a technology through redefining a problem to which an emerging technology can be seen as a solution (Bijker, 1995). Additional strategies include the use of rhetorical arguments, adopting the views of another group to criticize a technology from the outside, or forming alliances with key actors involved in the design/development process (Aibar, and Bijker, 1997; Bijker and Bijsterveld, 2000).
Applying the SCOT framework
3.1 As presented above, the SCOT framework is largely seen and used as an approach for historical studies of new technologies. Nonetheless, as Bijker (1997) notes, SCOT can be used for sociological studies of technology as well as historical ones. The case study presented here is an example of a sociological study of technology using the SCOT approach. From 2000 to 2003 I studied Connected Kids, a university-led IT project taking place in Troy, New York, in close collaboration with members of the local community. My research consisted of interviews with 37 members of the Troy and university community who were directly involved in the Connected Kids project. My research also involved participating in an email list serve for Connected Kids, and gaining access to transcripts of meetings on Connected Kids. These findings, the subject of the next sections, focus on Connected Kids' early phase of development from 1999-2001. The story I present here is reconstructed from interviews, transcripts, and observations made between 2000 and 2003. The actors and groups figuring in this story come from the city of Troy and the city's local university, Rensselaer Polytechnic Institute (RPI). Except for the two professors leading the Connected Kids project, Teri and Jim, all actors' names have been altered for confidentiality purposes[5].The story of Connected Kids
Relevant Social Groups and Stabilization
4.1 The story of Connected Kids began in the autumn of 1999, when Will, an official working in Troy's City Hall, approached Teri and Jim with a problem the city was facing regarding collaboration and communication among city not-for-profits. Will had known Teri and Jim through a number of previous encounters, one being a web design course taught by Teri and Jim at RPI. This course involved students with members of the Troy not-for-profit community to develop small, web-based projects that met some need of the organizations. Will took an interest in this course and became involved in the activities of the class, and through his involvement, he developed a dialogue with Teri and Jim on ways IT could be used to help meet certain needs in the Troy community. (Teri and Jim are the actual names of these two actors, although all other actors’ names have been altered in this article for confidentiality purposes. Teri and Jim, early on in this research, suggested that their actual identities be used.)4.2 The problem Will discussed with Teri and Jim in 1999 pertained to the recent closing of the city's Youth Bureau. This Youth Bureau had helped coordinate youth services among not-for-profits and disseminated information about these services to the wider public. Because the Bureau no longer existed, the City felt communication and coordination among the local youth organizations was suffering, and Will was curious whether an IT system might help support this lag in communication. Further, if communication and coordination could improve among not-for-profits, Will hoped this improvement might reduce the duplication of services provided in the city, and thus potentially save the city money.
4.3 Teri and Jim listened to Will's problem and his idea for developing an IT solution, and they agreed to work with Will. More particularly, Teri and Jim agreed to be the leaders for this IT project, and Will agreed to play a more supportive role in helping Teri and Jim gain access to city funds and local youth service actors who would be interested in participating in this project. By the end of the meeting, the three had made an informal agreement to work toward building an IT system that would house and distribute information about the city's youth services, programs, and events. The project was also given a name, that of Youth Online (the name 'Connected Kids' came later in the process).
4.4 Teri and Jim were excited about this venture. Both had research and teaching interests in IT design, although neither had actual experience in building an IT system:
I originally [only] wanted to research community networks [a type of computer-networking technology], but because there were no community networks [in Troy] to study, I had to build one! (personal interview with Teri, March 2000)
With respect to [this IT project], the single most important guiding principle for me has been Bakhtin's observation that we need other people to see what's behind our heads, i.e., to see what we cannot see for ourselves. (email correspondence with Jim, July 2001).
4.5 Thus, both Teri and Jim were inspired and guided, at least partially, by their previous research interests. These interests were complementary to the needs of Will, and through various interactions among these three, the idea for an IT system was born.
4.6 These early meetings reflect the idea of degrees of stabilization within two relevant social groups (RSGs). Teri and Jim represented one group, a group composed of professors from RPI and academia more generally, and Will represented the second group, a group composed of municipal officials and servants. Through their initial meeting, Teri, Jim and Will dictated an initial interpretation of this technology, that being an IT system that would house and distribute information on youth. Further, this technology was perceived as a) potentially solving particular problems in Troy, namely, communication among organizations and a financial problem for City Hall, and b) a type of research effort by Teri and Jim. In addition, through forming a definition for this technology and situating it as a solution to a problem, Teri, Jim, and Will had effectively formulated a semiotic structure around this particular artifact. This IT now had a (more or less) articulated interpretation that could be presented to other potential relevant social groups. The extent to which this semiotic structure would remain in place would depend on the kinds of processes and interactions surrounding and involving the technology. As will be seen, future influences would alter the technology's design, but the fundamental meaning of this technology as a type of IT system would remain intact.
Semiotic Structure and Technological Frame
4.7 Shortly after Teri, Jim, and Will formed the Youth Online project, they entered into a number of grant-writing activities to secure funds for Youth Online. This grant writing activity further clarified and stabilized various meanings for this technology, and the funding bodies to which these grants were written collectively represented a relevant social group that splintered into three subgroups.
4.8 The first grant was written towards the end of 1999 for the Howard and Bush Foundation. This Foundation gave Teri early feedback on her proposal, saying that they would like to see a prototype of Youth Online before agreeing to award money. Although no immediate plans were made, Will, Teri, and Jim quickly realized that a prototype would have to be built soon [an activity that will be explored in more depth in the next section].
4.9 This news that a prototype would be needed coincided with news of another possible grant; the corporation 3Com, a company that specializes in the manufacturing of networking equipment such as routers and switches, announced its "Urban Challenge" grant. This grant offered equipment to groups trying to build municipal (computer-based) networks. Teri and Jim first heard of this grant opportunity and they contacted Will, who had need for such technology after managing to convince the city in the previous year to lay down a conduit in downtown Troy. This conduit was Will's first attempt to build a network in Troy, yet the conduit still lay empty, with no immediate means of securing the necessary networking cable and equipment.
4.10 One criterion of the 3Com grant was that applicants specify a community need that the gifts of equipment would help fulfill. Teri, Jim, and Will offered a detailed description of the ways in which Youth Online was a needed technology for Troy. They described how this technology could hold media-rich content relevant for youth that could then be distributed to not-for-profits, kids, parents, and schools. The wide bandwidth found in a municipal network would be a necessary ingredient for distributing this material, and the equipment from 3Com would be one step in the direction of acquiring this bandwidth. To better reflect the networking potential of the database, they changed the name from Youth Online to that of Connected Kids[6]. This grant was submitted in April 2000 and was awarded in November 2000. The equipment received from this award was distributed to many of the not-for-profits in the area and was well received.
4.11 In the spring of 2000, Teri and Jim began to collaborate with a third RPI faculty member, Sara, from the Computer Science department, to write yet another grant proposal, this time to the National Science Foundation (NSF). This grant proposal was to gain funding for Connected Kids over the course of three years. In particular, the grant would allow for a range of participatory activities involving the larger Troy community in the development of Connected Kids, i.e. its design, testing, and continual development. In addition, the grant would fund PhD students in Computer Science and in Teri and Jim's department. These students would program Connected Kids functionality and design Connected Kids' interface. In spring 2001, NSF awarded the Connected Kids project $900,000 dollars over the course of three years, and this large sum of money would allow Teri and Jim to gather a group of student designers and programmers, plan for participatory activities with the local community, and purchase needed equipment for the project.
4.12 These grant-writing activities, and the interactions with funding bodies, had a lot of influence on clarifying the semiotic structure being built around this IT system, and also, brought further stabilization of the artifact's meaning for Teri, Jim and Will. The first grant written to Howard and Bush resulted in the need to build a prototype, which would act as a "reified" interpretation of Connected Kids as web-based technology housing information on youth for the Troy public. The second grant, written to 3Com, resulted in a change in name from Youth Online to Connected Kids, and this technology was situated as a "community need," i.e. a web-based technology that would provide media-rich information for youth. This second grant also clarified the multiple intended end-users, i.e. youth-service not-for-profits, local government, parents, children and youth, and schools, and each of these end-users became a relevant social group.
4.13 Thus, the semiotic structure, which was gaining more stability through these grant proposals, was now influencing which actors and social groups would become involved in later stages of the design process. The meaning of the technology, which was being presented to funding bodies and other groups, was thus closing down the range of other potential 'users' who could influence the system's design. Further, through these writing activities, Teri and Jim (in particular) were developing a more stable interpretation of the artifact for themselves, which they likewise presented to others.
4.14 Other tangential but highly relevant technologies were now becoming part of the process as well; these were the routers and switches awarded by 3Com, and these technologies' distribution to some of the intended end-users, arguably, contributed to the semiotic structure being built for Connected Kids. Here, words were not simply defining what Connected Kids was going to be, but physical artifacts, tangent and yet necessary for the use of the future system, were also providing material 'clues' as to Connected Kids' meaning, and thus they would arguably influence and shape how Connected Kids' purpose would be interpreted by these future, potential end-users.
4.15 Finally, as will be seen in a later section of the paper, the money awarded by the NSF grant would enable a number of activities to take place, in particular the involvement of hired student help, the purchasing of equipment, and holding focus groups and participatory design sessions with end-users. All of these events, led by Teri and Jim, would cumulate into a technological frame for Connected Kids, i.e. a frame containing both material and non-material elements that would further push Connected Kids' development down a particular path. Thus, taken together, the wording of the grant proposals, the subsequent distribution of the awarded technologies, and the acquired funding from NSF all contributed to Connected Kids' emerging development. They helped to solidify the semiotic structure and also provided material elements (primarily funds and needed technology) that would contribute to a technological frame. The next steps in the process would involve bringing in new actors and groups, and starting the process of building a physical, i.e. reified form, of the emerging technology.
Introducing Other Relevant Social Groups
4.16 Additional relevant social groups began entering the design process when Teri and Jim asked students in their web design course to volunteer to build the Connected Kids prototype requested by the Howard and Bush Foundation grant. A small group of students expressed their interest, and Teri and Jim began involving these students in Connected Kids activities. One such activity was a presentation of Connected Kids' potential to several representatives from youth-service not-for-profits, local government agencies and the local school district. This presentation took place in late February of 2000 in a public building downtown. In addition to informing members of the youth-service community of Connected Kids' potential, this meeting was designed to gain input from the community that could inform the students as they designed and built the Connected Kids prototype.
4.17 The invited participants in February's meeting listened to Teri and Jim's presentation and then discussed how Connected Kids might meet their needs. Several of these participants stayed throughout the afternoon to look at various examples of online databases for youth services that currently existed on the web. These participants gave feedback to these examples, and offered their ideas of what they would like to see in a similar technology built for Troy. This feedback was noted down by the students who were working on designing the prototype, and these students announced to the group that they would build a prototype based on what they had heard that day.
4.18 Through presenting Connected Kids as a solution to problems in the youth-service community, and through also presenting examples of youth databases to launch a discussion on design features for Connected Kids, Teri and Jim were guiding and involving these actors according to the semiotic structure that had already been built. Thus, Connected Kids was presented as a type of "online system" and a "solution" for the youth-service community. In addition, audience members' reactions were limited to what was being presented; issues, problems, and interpretations outside the scope of this presentation were thus less likely to emerge in later discussions. Thus, although each relevant social group was now interacting with Connected Kids and starting to develop their own interpretation of Connected Kids, much of these interpretations would build on the semiotic structure already surrounding Connected Kids.
Further Stabilization and Further Framing
4.19 The academic year of 2000-2001 was a critical period for the technological frame forming around Connected Kids. During this period, a number of problem-solving strategies, tools and technologies were starting to become regular aspects of the Connected Kids process. For example, a regular strategy used for making design decisions regarding Connected Kids was the use of focus groups and/or participatory design sessions. The first series of such meetings occurred in October 2000, where the prototype was formally presented to the youth-service community. These meetings were structured as focus groups, and were aimed to gain feedback on the newly created prototype. This information from these focus groups was then used by Teri, Jim, and RPI students to develop a set of design specifications. In an email sent to the Connected Kids' participants in March, 2001, Jim offered a summary of the information gathered from these focus groups and how that information would influence Connected Kids:
Based upon what you have told us, we perceive a need to develop a database that has sufficient stability and coherence to be functional and easy to use for any and every youth-services organization and that offers at the same time a maximum of freedom and flexibility for individual organizations and individual users. We anticipate that we will be able to provide a simple and easy-to-use interface that will permit input information about their mission and services, plus contact information. We also expect to be able to provide different interfaces for organizations, parents, and kids, and we are planning to provide opportunities for young people to display their own creative work (email correspondence, March 26, 2001).
4.20 Jim's e-mail summarizes his (and other RPI actors') view of participants' needs and discusses design decisions that would be incorporated into Connected Kids' interface and functionality. In articulating these design specifications to the participants, Jim was further strengthening the semiotic structure around Connected Kids. The next steps then involved translating these design criteria into programming code.
4.21 The first attempts to translate design criteria into programming code began at the end of 2000 and continued into 2001. During this time, Teri and Jim began organizing another set of group meetings, called 'design sessions' to show the youth-service community the current status of Connected Kids and gain these participants' feedback. Once again, the strategy was to involve end-users through a planned group activity to further specify Connected Kids' design. These design sessions, which were funded by the NSF award, took place in autumn-winter 2001: participants tried and tested the interfaces and functionality that had thus far been developed for Connected Kids. RPI students were on hand to demonstrate the technology to participants and answer their questions. These sessions were also videotaped and transcribed to give Teri, Jim, the student designers and programmers feedback on how Connected Kids was meeting the youth-service community's needs. New adjustments were made to Connected Kids' interface and functionality based on this feedback. Additional sessions were organized in the spring of 2002 for youth and parents, and on-sight user-tests were organized for autumn 2002. Once again, these sessions were designed to gain feedback to further guide Connected Kids' ongoing construction.
4.22 Through this iterative process of developing Connected Kids, presenting Connected Kids to relevant social groups, and translating these groups' feedback into Connected Kids' design, Teri and Jim were purposefully attempting to reflect relevant social groups' preferences in the technology. This iterative process, moreover, had become these actors' main strategy for moving Connected Kids' design forward. Thus, the frame around Connected Kids, which included these design sessions, further strengthened and hardened, and as a result, Connected Kids became further stabilized.
4.23 To be sure, the involvement of end-users in design sessions influenced Connected Kids, yet the extent to which these end-users could influence Connected Kids' final design was constrained by the semiotic structure that had been built initially by Teri, Jim and Will. Wendy, one of the students involved in designing and building Connected Kids, spoke about the limits of these actors' influence in the following way:
As far as making decisions, the users were not … there, at the table with us, making decisions about the database or the interface. They supplied the spirit of what they needed and also the raw material and we were left to turn that into [design] requirements (personal interview, September, 2003)
Epilogue
4.24 My data gathering period ended in 2003, at which time Connected Kids had not yet reached closure. However, one can now find Connected Kids online, as a fully-functioning IT (http://www.connectedkids.info). As the description on the site states, Connected Kids is "a Web-accessible database providing…information about area youth-services organizations; information about these organizations' programs, services, and activities for learning, arts, sports, recreation, socializing, and counseling; and images of young people engaged in educational, recreational, and social activities" (accessed 20 February 2009). In other words, Connected Kids finally hardened into an artifact, and its current meaning is similar to the one proposed by Teri, Jim and Will eight years earlier. Although the basic meaning of Connected Kids never altered much in the course of its development, i.e. it was and always remained a networking technology intended for youth and youth-service providers, various design specifications were made along the way, and these design specifications translated into subtle, yet important differences for the intended users of the system.
Reflecting on SCOT: The role of resources
5.1 The story of Connected Kids illustrates many of SCOT's concepts and demonstrates the usefulness of this approach. The concepts provide an analytical vocabulary for making sense of the interactions that surround and give rise to a particular artifact. In fact, although Connected Kids is more a tangent technology than a new innovation[7], the amount of rich, complex interactions brought to life by a SCOT telling illustrates how different kinds of artifacts – not just new technologies -- can be described and explained through this approach.5.2 Yet in providing such a rich description, a SCOT analysis can also lead to cloaking the strongest influences in a technology's design. In the case of Connected Kids, these influences took the form of key resources – knowledge, infrastructure, and money – that were found either within the walls of RPI, or easily attained by virtue of association to RPI. For example, as professors at RPI, Teri and Jim had access to a range of resources that included sophisticated IT infrastructure, a tech-savy student body, and talented academics from a range of disciplines. This wealth of talent and infrastructure translated into elements of RPI's technological frame that were present at the time Connected Kids began and that continued to be influential throughout the duration of the project. In addition, as academics at a technological institute, Teri and Jim were able to translate Connected Kids as a type of 'research,' a strategy that helped them gain NSF funds. These funds, moreover, enabled Teri and Jim to hire programmers and designers, host meetings with participants, and buy necessary equipment. Taken together, as actors embedded within RPI, Teri and Jim held a strategic advantage that enabled them to gain access to and make good use of key resources and strategies that collectively shaped a particular trajectory for Connected Kids.
5.3 Thus, even after demonstrating many SCOT insights, such as i) how multiple actors and groups entered the process at different stages; ii) the ways in which Teri and Jim made use of micro-political strategies to shape Connected Kids' path, and iii) the nonlinear development that Connected Kids took, one could still argue that much of Connected Kids' success depended upon the existence of an institute such as RPI and on actors such as Teri and Jim, who were willing to make good use of the resources found within such an institute. In short, these resources, and the fact that Teri and Jim had access to these resources, were critical determinants to Connected Kids' unfolding.
5.4 I am fairly certain that a SCOT analyst would resist any kind of simplistic description of the sort I just gave, i.e. pointing the finger too strongly in the direction of just one group of actors and/or institute would violate one of the main aims of this approach, i.e. to reveal the multiple social influences that shape a technology's development. Yet in my mind, the strength of SCOT is also its weakness, as highlighting the complexity of technology design can lead very easily to cloaking the simple and obvious. With Connected Kids, the simple and obvious was the role of money, technological resources, and the high amount of initiative exhibited by Teri and Jim.
5.5 I am also aware that the resources and strategies I describe above could arguably be placed under the rubric of RPI's technological frame. Some might indeed argue that these resources and their influence would be accounted for simply by making use of this term. Yet placing these under the larger category of technological frame, a category that takes into account any and every kind of structural influence[8], seems to undermine the importance of resources in this particular case study. Again, by allowing the notion of a 'technological frame' to account for so much, I find that the term has ended up actually hiding more than revealing what is actually important in shaping Connected Kids.
5.6 Thus, to more fully unpack and highlight the role resources played, I would like to walk the reader through a re-analysis of my data, looking carefully at the ways in which resources are discussed in interviews, and how these resources can be resituated within the context of technological frames.
A potential way forward: a second look at resources
6.1 A second look at the ways in which money (in particular) and resources (more generally) were discussed among participants revealed how these respondents were, consistently, linking ideas of influence and power with perceptions of who had which kinds of resources. For example, several respondents described certain Troy members as being "big players" or "highly influential", and their explanations for these descriptions often times lay with their perceptions of who had access to certain kinds of resources. One respondent referred to these powerful figures as the "big fish" in the community who "ate up" all the available resources, leaving the "little fish" to simply get by on what was left (personal interview, May 2000). Other respondents discussed the role resource distribution played in forming community ties:[that organization]… They're ruthless and influential. They're ruthless in going after more funding, larger programs, going after the bigger piece of the pie. They work their connections (personal interview, summer 2001).
6.2 Relations were thus tense among some of these respondents, and all relations seemed loaded with the underlying issues of who had more or less access to money, programs, and other kinds of resources such as IT infrastructure and technological knowledge.
6.3 To look at which resources respondents labeled as important, I decided to adapt the table used by Bijker (1995) to illustrate the elements found in a technological frame. In the table shown below, I list the original technological frame elements outlined by Bijker (1995), and I add to this list the elements of "key material resources"[9] as another structuring influence.
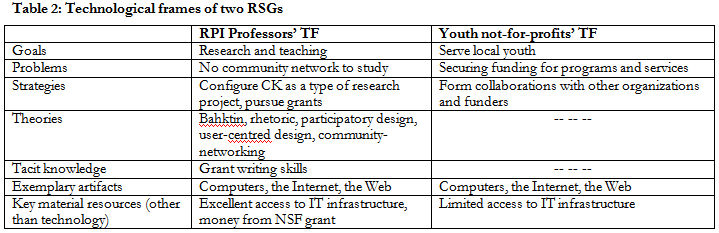
|
6.4 Next, under each element heading in Table 2, I describe what items are included in the element (e.g. "money from NSF" under the element "key material resources"), and in some cases, I have also attempted to convey a sense for how one technological frame might have "more or less" of a particular element compared to a different technological frame. Thus, for example, under "key material resources" I list "excellent access to IT infrastructure" under RPI's frame, and I state "limited access to IT infrastructure" under the youth not-for-profits' frame. This access to IT infrastructure was slightly different, in my mind, to the presence or absence of the Internet (which is placed under "Exemplary Artifacts"): the Internet existed as a "real" technology with which all relevant social groups interacted, yet access to this technology and other ITs varied considerably from one not-for-profit to the next, and none of the not-for-profits held such good access as RPI.
6.5 Because ideas of more or less resources loomed large in the minds of respondents, I started to rank these resources according to the perceptions of respondents. Thus, as a third step, I elaborated upon the technological frame element of "material resources" according to the relative access each relevant social group had to each particular resource:
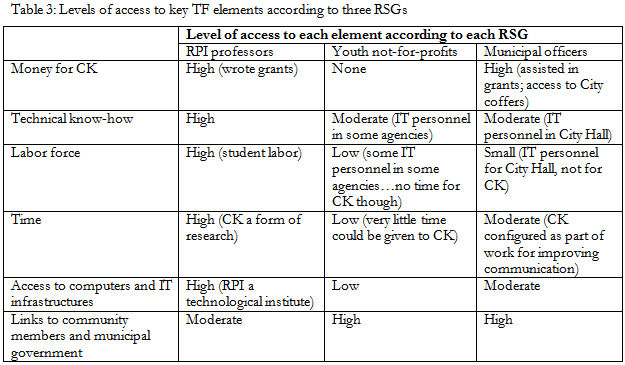
|
6.6 Here, in Table 3, each relevant social group's relative access to a particular resource is given, and this results in a ranking scheme of "low," "medium," and "high" access for each resource. RPI professors are thus shown as having higher access to the majority of resources listed. In contrast, youth agencies have relatively low access, and municipal officers vary in their levels of access. Such a ranking derived from respondents' comments, and the results highlight the general sense I had gained from the interviews that i) resource access was an important concept in this study; ii) that RPI was seen to have more than others in the community; and iii) those actors who played more powerful roles in Connected Kids' construction tended to have more access to these kinds of key resources.
Linking back to SCOT
7.1 The above analysis is not to be taken, necessarily, as a replacement for using "technological frames", but rather demonstrate how an analysis of a technological frame could benefit from a more careful break-down of the different elements involved. As technological frames are quite complex, involving a wide array of socio-cognitive-material elements, they could easily confuse an analyst versus sharpen an analyst's eyes to the structures important for a given technology project[10]. Further, as technological frames are the only structural concept in SCOT that take into consideration how structures within a wider social context can influence a technology, then I believe analysts should spend more time delving into this concept to ensure that important structural considerations are not overlooked.7.2 My strategy has thus been a reworking of the technological frame elements to highlight their relative contributions. Further, this re-analysis was done (partly) as a result of my own reflections, but also in light of the comments I received from my respondents; although it was clear from my own observations and interviews that Teri and Jim were, from the start, the most prominent actors in Connected Kids' construction, and that their role had much to do with their inclusion in the RPI frame, my respondents' comments regarding resources and power reinforced the need to pay more attention to the relationships between resource-access and the actions of certain actors. Thus, extending my analysis to focus more squarely on the role of resources came from one of the fundamental tenets of SCOT, i.e. following the actors.
7.3 Following the actors in the context of field work involves skilled, open-ended interviews with actors, and multiple trips into the field to follow-up on themes that have emerged from previous interviews. Thus, forming one's own categories and concepts from the data is as equally important as understanding how the data might (or might not) reflect the concepts proposed by a theory. Such tacking back and forth between theory and data is what skilled qualitative researchers do in using a range of hermeneutic approaches (Briggs, 1996; Bleicher, 1982; Denzin, 1989; Denzin and Lincoln, 2008; Kvale, 1997; Harrington, 2001), and it is through a balance of knowing theory (which would include but not be limited to SCOT) and performing good research that more complete tellings of socio-technical processes can be told. In doing so, a better understanding can be attained of the ways actors and groups can have different power relations with technology, and how such relations ultimately affect the technologies that surround us.
Conclusions
8.1 This case study of Connected Kids has achieved much in showing the value of the SCOT approach. My SCOT telling and subsequent reflection have been, I believe, more complement than complaint. In following the actors, I realized that certain structural considerations, i.e. the role of resources and resource-access, needed a more detailed approach to the role of technological frames. As other writers have commented on the strengths and weaknesses of the SCOT approach from a more theoretical angle, I believe the more fruitful direction for future research lies in bottom-up approaches to studying technology. ((Winner, 1993; Klein and kleinman, 2002; Russell, 1986). Such approaches will, most likely, result less in grand theories of socio-technical processes, and more in rich, insightful descriptions of the complexities of technology design, where structure and agency are given attention as needed by the case study at hand.Notes
1 Some of these critiques are discussed at the end of this paper, yet there are others the reader should be aware of, and these include Buchanan (1991); Clayton (2002); Douglas (1990), Edgerton (1993), Haard (1993), Rosen (1993), and Williams and Edge (1996).2 During the time of this research, both project leaders were faculty members at RPI. Since this time, however, one member has moved to SUNY, Albany.
3 Haard (1993) notes that this traditional view of closure as resulting from consensus needs to be challenged; technologies can easily result from a long chain of conflicts among groups, not just through a process of consensus.
4 Although see Kline and Pinch (1996) for an example of how end-users can reopen the process of interpretive flexibility of an artefact.
5 Teri and Jim's names have been left intact after early consultations with them about how to handle their identity, as they themselves were publishing and discussing their work on Connected Kids.
6 In the interest of simplicity, and to not confuse the reader, I will continue from now on to refer to this technology as Connected Kids.
7 The current study differs slightly from a "typical" SCOT one in that a new application of an otherwise "hardened" artifact is being studied: in the present study, I am looking at an emerging IT system where major components of this IT system (e.g. computers, the Internet and Web) had long since hardened into artifacts prior to its creation. I would like to point out, however, that the SCOT approach has already been applied to topics such as town-planning, where the "technology" in question was a wall and a city's extensions (Aibar and Bijker, 1997). Thus, SCOT seems to be fairly pliant and adaptable to a variety of different artifacts.
8 As an analytical concept, "technological frames" is intended as a "heterogenous concept" that accounts for material and nonmaterial structures that can influence socio-technical design (Bijker, 1993: 120-121). Yet many have struggled with SCOT's handling of structure, and the use of technological frames in particular. As Klein and Kleinman (2002) note, "technological frames" ignore the wider contexts and larger structures in which technology developments take place, and it disregards the role institutions can play. Stuart Russell (1986) criticizes SCOT for ignoring such social structures as class and how relevant social groups relate to other sections of society, notably larger economic, political, cultural and ideological structures. Russell also critiques Pinch and Bijker (1984) for portraying social groups as effectively equal in power, i.e. a pluralistic view of society. Russell's (1986) critique is echoed by Winner (1993), who criticizes the SCOT approach (alongside other social constructivist approaches) for ignoring larger, underlying dynamics and structures that influence technology design. My criticism is slightly different: I found the heterogeneity of this concept difficult to work with, i.e. it cloaked certain aspects of structure versus illuminate them.
9 The idea of key resources can be expanded upon in future research to include more non-material aspects such as knowledge expertise and diversity of knowledge sources. Indeed, in other parallel research, the author is currently exploring these themes (Prell, 2009).
10 Russell (1986) also critiques Pinch and Bijker (1984) for portraying social groups as effectively equal in power, i.e. a pluralistic view of society. In some respects, I found SCOT's view of structural influences as being similar to this pluralistic take on society, i.e. that tehnological frames were just one of the many influences on a technology's design, and further, that many elements could fit under this category, all of which are potentially of equal importance.
References
AIBAR, E. and Bijker, W. 1997. Constructing a city: The Cerda plan for the extension of Barcelona. Science, technology, and human value 22:3-30.
BIJKER, W.E. 1993. Do Not Despair: There Is Life after Constructivism. Science, Technology, & Human Values 18:113-138. [doi:10.1177/016224399301800107]
BIJKER, Wiebe E. (1997): Of Bicycles, Bakelites and Bulbs. Cambridge, Mass.: MIT Press.
BIJKER, W.E., and J. Law. 1992. Shaping technology/building society : studies in sociotechnical change MIT Press, Cambridge, Mass.
BIJKER, W. and Bijsterveld, K. 2000. Women walking through plans: technology, democracy, and gender identity. Technology and culture, 41: 485-515.
BLEICHER, J. 1982. The hermeneutic imagination: outline of a positive critique of scientism and sociology. Routledge & K. Paul, London; Boston.
BRIGGS, C. 1997. Learning how to ask: A sociolinguistic appraisal of the role of the interview in social science research. Cambridge university press, Cambridge.
BUCHANAN, R.A. 1991. Theory and Narrative in the History of Technology. Technology and Culture. 32 365–76. [doi:10.2307/3105715]
CLAYTON, N. 2002. SCOT: Does it answer? Technology and Culture 43: 351-360. [doi:10.1353/tech.2002.0054]
DENZIN, N.K. 1989. The research act: a theoretical introduction to sociological methods. 3rd ed. Prentice Hall, Englewood Cliffs, N.J.
DENZIN, N.K., and Y.S. Lincoln. 2008. Strategies of qualitative inquiry. 3rd ed. Sage Publications, Thousand Oaks, Calif.
DOUGLAS, S.J. 1990. The social construction of technological systems: New directions in the sociology and history of technology. Isis 81: 80-84. [doi:10.1086/355252]
EDGERTON, D. 1993. Tilting at Paper Tigers. The British Journal for the History of Science 26:67–75. [doi:10.1017/S0007087400030144]
HAARD, M. 1993. Beyond harmony and consensus: A social conflict approach to technology. Science, Technology, & Human Values 18: 408-432. [doi:10.1177/016224399301800402]
HARRINGTON, A. 2001. Hermeneutic dialogue and social science : a critique of Gadamer and Habermas Routledge. London ; New York.
KLEIN, H. and Kleinman, D. 2002. The social construction of technology: structural considerations. Science, technology, and human values 27: 28-52. [doi:10.1177/016224390202700102]
KLINE, R. and Trevor Pinch. 1996. Users as agents of technological change: The social construction of the automobile in the rural United States. Technology and Culture 37:763-795. [doi:10.2307/3107097]
KVALE, S. 1996. Interviews: An introduction to qualitative research interviewing. SAGE, London.
MACKENZIE, D. and Wajcman, J. 1999. Introductory essay: the social shaping of technology. In The social shaping of technology., edited by D. MacKenzie and J. Wajcman, 3-27. Philadelphia: Open University Press.
MARTIN, B. and Scott, P. 1992. Automatic vehicle identification: A test of theories of technology. Science, Technology, & Human Values 17: 485-505. [doi:10.1177/016224399201700404]
PINCH, T.J., and W.E. Bijker. 1984. The social construction of facts and artifacts: Or how the sociology of science and technology might benefit each other. Social studies of science 14:399-442. [doi:10.1177/030631284014003004]
PINCH, T.J., and Bijker, W.E. 1987. The social construction of facts and artifacts: Or how the sociology of science and the sociology of technology might benefit each other. In The social construction of technological systems: New directions in the sociology and history of technology, edited by W.E. Bijker, T.P. Huges and T.J. Pinch, 17-50. Cambridges, MA: MIT Press.
PINCH, T.J., and W.E. Bijker. 1986. Science, relativism and the new sociology of technology: reply to Russell. Social studies of science 16:347-360. [doi:10.1177/0306312786016002009]
PRELL, C. 2009. Linking social capital to small-worlds: A look at local and network-level processes and structure. In special issue of Methodological Innovations online, edited by Nick Crossley, John Scott, and Christina Prell, 4: 8-17.
ROSEN, P. 1993. The social construction of mountain bikes: Technology and postmodernity in the cycle industry. Social Studies of Science 23: 479 – 513. [doi:10.1177/0306312793023003003]
RUSSELL, S. 1986. The social construction of artifacts: a response to Pinch and Bijker. Social studies of science 16:331-346. [doi:10.1177/0306312786016002008]
WILLIAMS, R. and Edge, D. 1996. The social shaping of technology. Research policy 25: 865-899. [doi:10.1016/0048-7333(96)00885-2]
WINNER, L. 1993. Upon opening the black box and finding it empty: Social constructivism and the philosophy of technology. Science, Technology & Human Values 18: 362-378. [doi:10.1177/016224399301800306]

